2 minutes
Simple Analyst Evasion
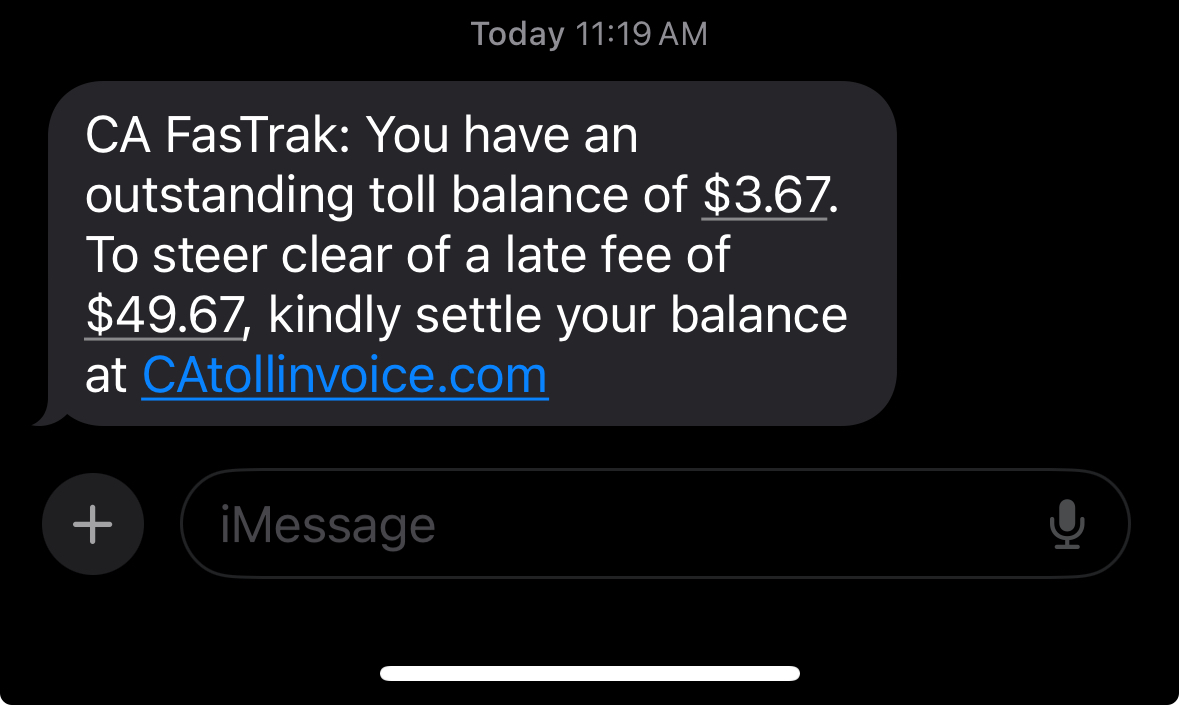
Phish message
A family member (aka Jane) was scammed with this message and asked me to take a look at the link for them
Scam context: CA Bay Area bridge tolls are sent out weeks or months later. A notice that you have a bill that is going to be escalated to a fare evasion fee if you don’t pay immediately is very common for bay area residents. However, however official bills only come via mail not sms.
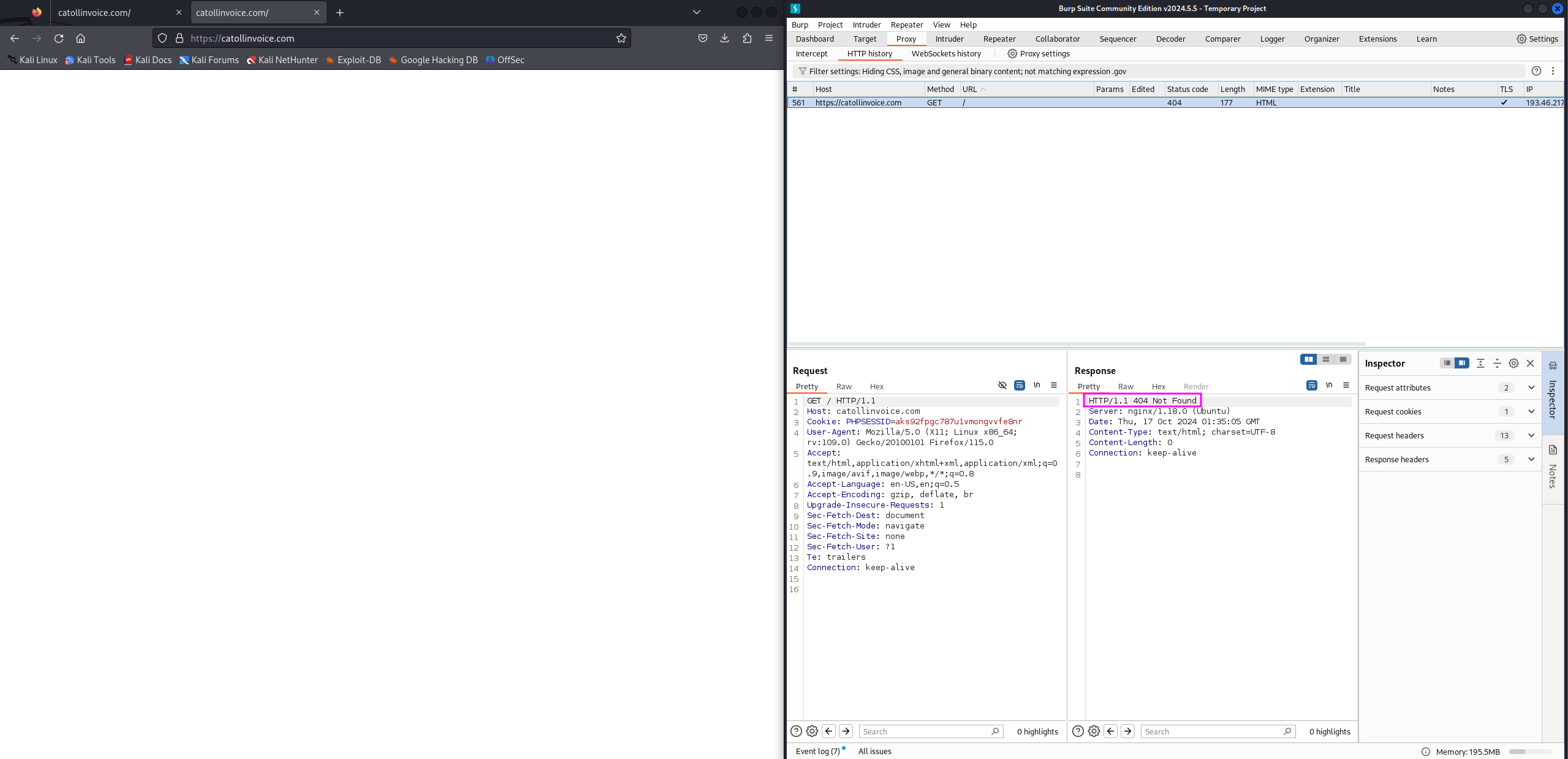
From my analysis machine you can see that we just get a 404
At this point I assumed the scammers had ended their campaign so I searched to see if I could find any other instances that showed what this link delivered Every other post appeared to 404 as well, but these were posted days before Jane was scammed
 https://www.youtube.com/watch?v=Z-oMukdokMo
https://www.youtube.com/watch?v=Z-oMukdokMo
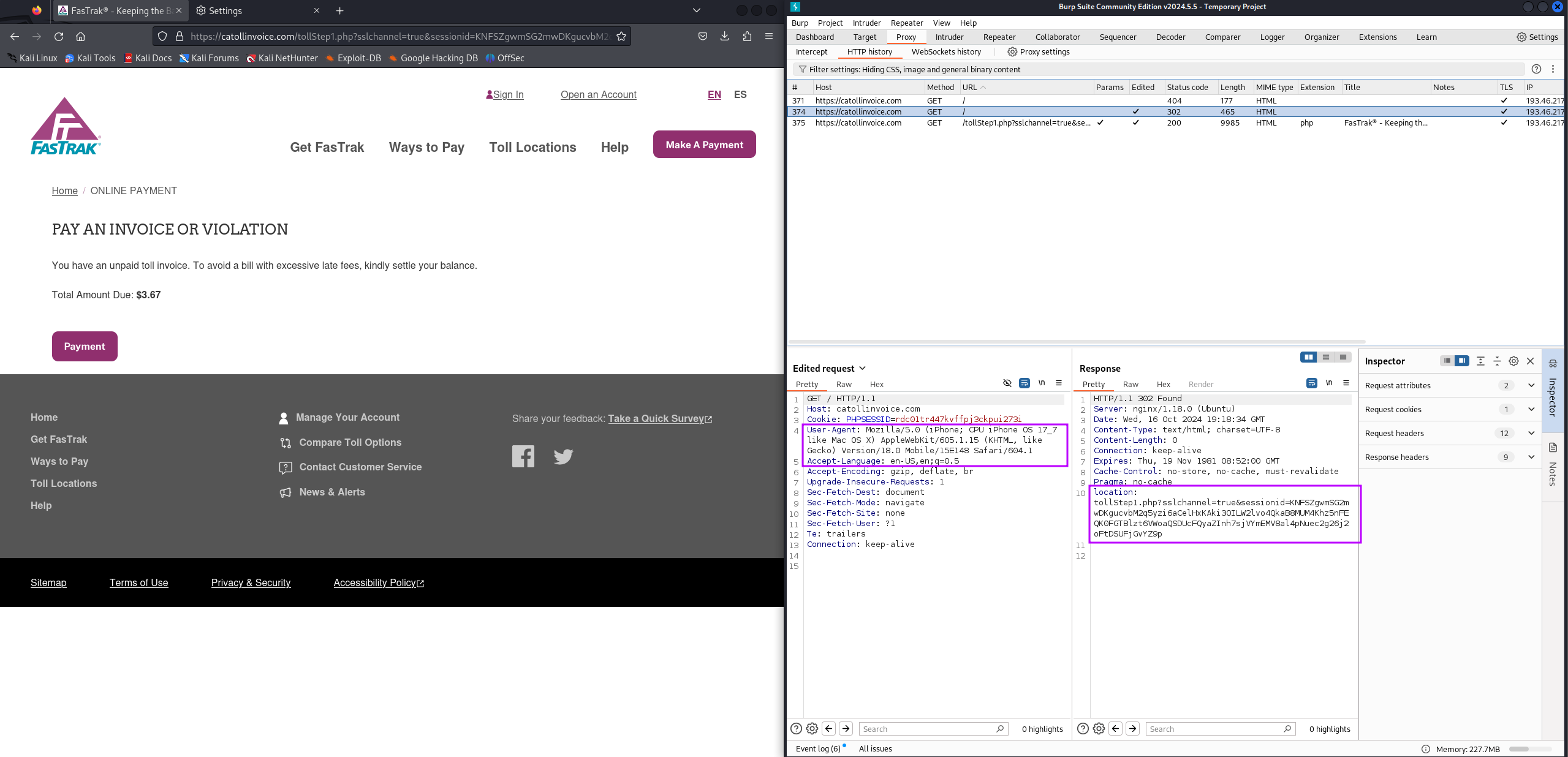
Taking a look back at Burp I realized the server was running nginx
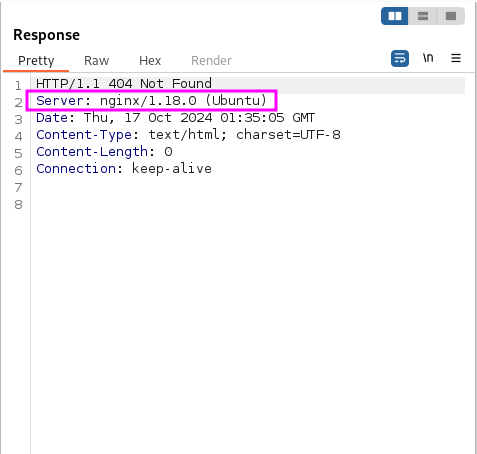
Nginx is an incredibly simple web server and reverse proxy When used as a reverse proxy Nginx can redirect requests based on many factors including subdomain, port, URI path, or user agent by specifying in the main config
Since this was sent via SMS I intercepted the request and used an iOS useragent giving the 302 to tollstep1.php which is the FasTrak impersonation page